Backup Appliance: How to Simplify Backup and Gain More Control
Table of contents
Complicated systems, dispersed data, information silos, and pressure to simplify. IT environments today balance the need for security with limitations of time, people, and budget. Storware Backup Appliance addresses these challenges—combining simplicity, automation, and a Zero Trust philosophy in one ready-to-use device.
Although there’s increasing talk about the need to simplify IT infrastructure, many server rooms still operate with isolated data repositories. Information is stored and managed in separate systems, which makes it difficult to share data between teams and departments within an organization. Such data dispersion limits monitoring capabilities and hinders the detection of unauthorized activities. It’s hard to protect what you can’t see and don’t have full control over. Each of these “silos” may require a separate approach to backup and Disaster Recovery, further complicating backup and data recovery processes.

Another challenge is the phenomenon of data gravity—the tendency of large data sets to attract applications, services, and additional resources. The more data accumulated in one place, the harder and more expensive it is to move. Migrating a large repository from an on-premise server room to the public cloud can take days or even weeks—or require physical transport of media. Meanwhile, new applications are being developed in the same environment that—instead of using distant services—opt for fast, local data access.
At first glance, data gravity and data dispersion seem to be opposing phenomena. In practice, however, they coexist and reinforce each other. Data remains in silos not because there’s no need for consolidation, but because its migration is often too expensive, time-consuming, or risky. In other words, it “gravitates” to a specific environment (local or cloud) and stays there.
Siloses stem from organizational, technological, and cultural divisions, while data gravity results from physical and economic processing limitations.
A real-world example: the sales and marketing department uses a CRM system in a SaaS model, with customer and campaign data located in the public cloud. In contrast, the finance department works on a local ERP system, whose data is stored on an SQL server within the company. As a result, each department operates in its own digital world, and collaboration—such as analyzing the impact of a marketing campaign on sales—becomes difficult. Migrating ERP data to the cloud involves process reengineering, significant costs, and risks.
Meanwhile, IT departments are fighting on many fronts. They handle routine, urgent tasks that—though essential—don’t add significant strategic value. They are also often responsible for the entire infrastructure: from hardware and software to configuration and user support.
Backup? It’ll Get Done After the Failure… Still Relevant Pitfalls in Data Security Thinking
A separate, but extremely important issue remains the attitude of clients themselves. Many companies still ask themselves: “Why do I need a backup if everything is working?” or “Why change systems if the current ones are functioning flawlessly?”
Costs are the most frequently cited barrier to investing in new solutions. Often, the only argument that convinces management to act is… a failure. Even in large organizations employing hundreds of people, it happens that management consciously limits IT and security spending, literally waiting for an incident to occur.
Meanwhile, regulatory pressure is growing—another regulation is set to come into force in June, expanding data protection obligations to all key companies. This will be a quick and, for many, surprising change. Despite this, the thinking that “it doesn’t concern us” still prevails. However, in today’s reality, attacks, ransomware, and incidents are not a matter of “if,” but “when.”
It’s also worth emphasizing that although the price of storage per terabyte is regularly decreasing, maintaining a consistent, secure data environment still requires investment—in people, procedures, and technologies.
Furthermore, a new, dangerous illusion has emerged: that migrating to the cloud—for example, to Microsoft 365 or Azure—relieves the organization of responsibility for backup. This is a myth. The responsibility for data protection and recovery still lies with the client. Cloud providers are responsible for the infrastructure, but not for user data.
Less Sometimes Means More
In an era of relentless cyberattacks, information security is of fundamental importance. What matters is not just the backup itself, but also the speed of reaction, reliability, readiness for change, and ease of management. Equally important are: intuitive device operation, universality, and seamless integration with both local infrastructure and the public cloud.
Our approach focuses on maximizing the simplification of IT systems. On one hand, we provide comprehensive data protection; on the other, we reduce the need to maintain separate backup systems, which are often expensive and complicated to operate. We operate on the principle that sometimes, less means more.
Storware Backup Appliance is a ready-to-use device that integrates hardware with software. Setup takes just a few minutes, and configuration and daily operation are almost maintenance-free.
The solution is based on the ZFS file system, which guarantees: data integrity, advanced compression, easy snapshot creation, and deduplication providing up to 5:1 space savings.
Backups are performed synthetically, and the appliance’s architecture allows for efficient operation even under heavy load—the only potential limitation is the client’s network infrastructure.
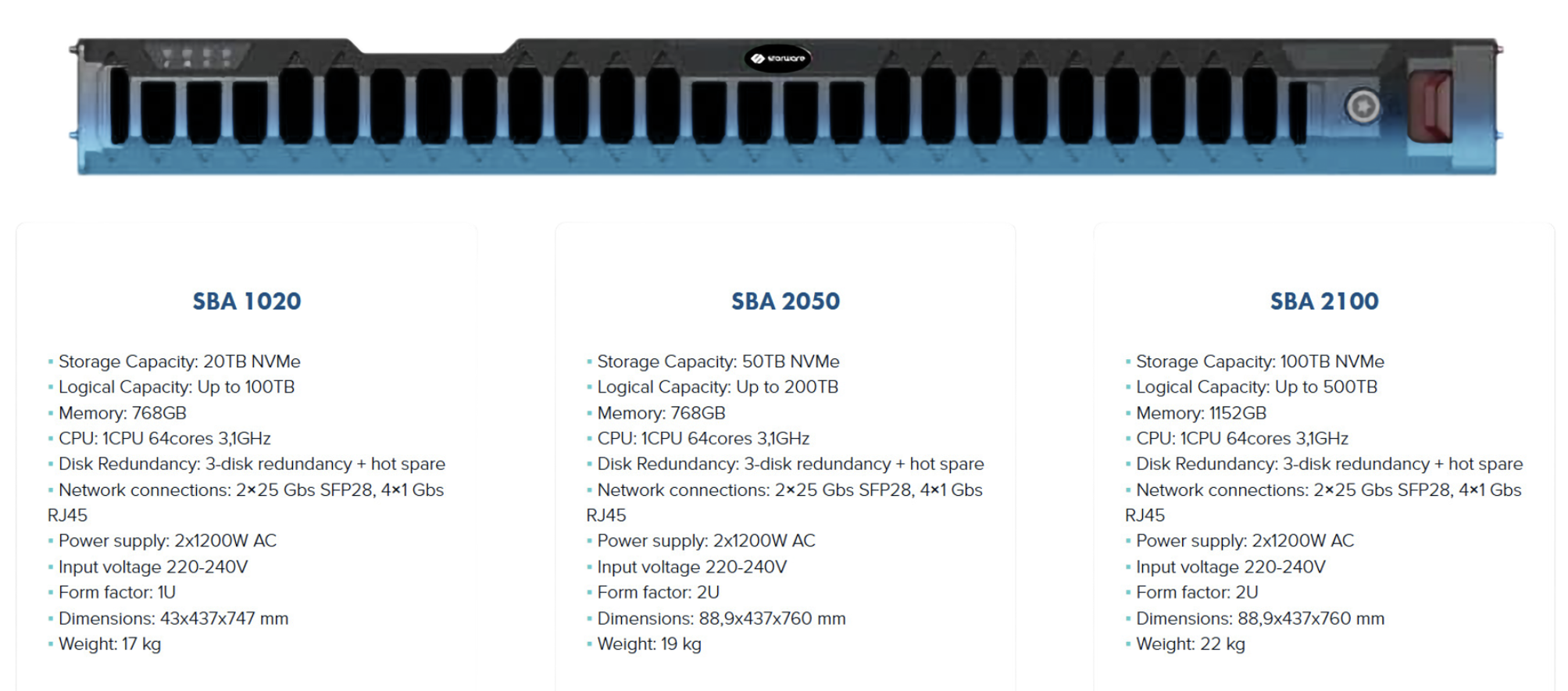
Storware Backup Appliance is available in three variants: SBA 1020 (maximum capacity 100 TB), SBA 2050 (up to 250 TB), and SBA 2100 (up to 500 TB). The solution not only secures data but also ensures its efficient storage. Thanks to ZFS deduplication, it’s possible to achieve up to 5:1 space savings. Backups are created synthetically, and the appliance’s architecture allows for efficient operation even under heavy load—the only potential bottleneck might be the client’s network infrastructure. Expected performance is approximately 0.5 TB per hour for a 64 KB block or 7 TB per hour for 512 KB.
Do It Yourself? Not Necessarily
An alternative to ready-made backup solutions are so-called DIY backup appliances—environments created and configured independently by IT teams, often based on existing infrastructure. This approach might seem cost-effective, but in practice, it involves greater complexity, risk, and a lack of unified technical support.
In the event of a failure, there’s no single point of contact—the responsibility for analyzing and solving the problem falls entirely on the internal team. This requires not only specialized knowledge but also the availability of people and resources 24/7.
DIY can be a good choice for organizations with large IT teams and very specific requirements. For most companies—especially those prioritizing simplicity, security, and reliable support—complete platforms provided by specialized vendors are a better solution.
Every Storware appliance is prepared individually—with a pre-installed and configured operating system, backup environment, and optimal settings. Once connected to the infrastructure, the device is ready to work—without time-consuming configurations and the risk of errors. The solution is based on enterprise-grade components: server processors, ECC memory, and disk systems optimized for intensive write operations and data deduplication. This is not just an ordinary server, but a specialized environment for data protection.
Of particular note is Paranoid Mode—a unique, proprietary RAID configuration that ensures continuous operation even in the event of a simultaneous failure of four disks. The automatic failover mechanism works automatically—without the need for administrator intervention.
Storware Backup Appliance supports a wide range of environments: virtualization (VMware, Hyper-V, KVM, Citrix, Nutanix, VergeOS), clouds (AWS, Azure, Google Cloud), container platforms (OpenShift, OpenStack), and physical infrastructure. One device provides consistent protection for all these environments—physical, virtual, and containerized—from a central point.
Security and Simplicity – Storware Backup Appliance in Practice
Modern IT environments demand solutions that are not only effective but also as user-friendly as possible and secured at multiple levels. Storware Backup Appliance demonstrates how these goals can be achieved in practice, based on the Zero Trust philosophy, intelligent automation, and a high level of component integration.
One of the key security elements in this solution is the use of the ZFS file system, which ensures not only data integrity but also effective protection. Data is stored by default on an encrypted ZFS pool, which is not automatically decrypted after a restart—physical password entry by the user is required.
The system also utilizes a TPM module, which enables automatic decryption of system partitions and those containing the library and database. This ensures the device remains fully operational, while simultaneously preventing an attacker from reading stored information if the disks are physically seized. Data access is secured in multiple layers. The end-user receives a 20-character encryption key, and for technical support, access to deeper system layers requires additional login credentials—complex passwords and 2FA authentication, available only to selected individuals within support and sales structures. The entire procedure is centrally documented, and access to the most critical components is secured with additional passwords and physical keys. This approach—though it may seem overly cautious—effectively prevents unauthorized access, even in the event of physical seizure of the device.
Storware Backup Appliance proves that a high level of security doesn’t have to mean complexity. On the contrary—properly designed mechanisms integrating encryption, access control, and automation create a system that is simultaneously easy to use, resistant to physical attacks, and compliant with best security practices.
